CODE APPLIED AT THE SOURCE
Digital files, including media and documents are encoded at the source. It takes less than four seconds and there is no room for error.
XSETTE UTILIZES A COMBINATION OF:
- Encryption (BMUS)
- Authorization (Node Pairing)
- Authentication (Watermarking)

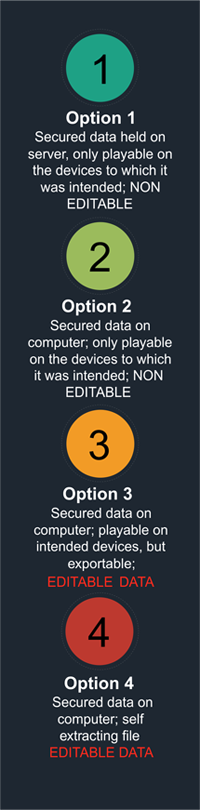
4 OPTIONS FOR ENCODING DATA
WE USE A PROCESS CALLED BMUS
Block management unification system – Our technology disrupts the serial delivery of digital content in a way never seen before, leaving it un-hackable.
IT'S INFURIATING TO HACKERS AND THIEVES

Most data protection companies use a simple process of encryption. This leaves data vulnerable. Encrypted data can be intercepted and decoded, leaving passwords, bank data and personal info in the hands of criminals. The rise and proliferation of malware and other forms of cyberattacks is a growing concern for both consumers and organizations of all sizes This leaves a huge question mark over certain data protection methods.
CURRENT ENCRYPTION CAN BE HACKED
- Simple Watermark – Can be filtered and removed
- Pure Encryption with a single cypher – Keys are routinely broken and distributed.
- Password – Once shared, it’s no longer secure.
- Special Encoding – Once the encoding is analyzed, it can be duplicated and distributed.
WE ARE CHANGING THE RULES
We change the way files are delivered by randomizing the data in multi-dimensions and scrambling the digits to a non-serial delivery. When normal encryption scrambles data files one or two layers, XSETTE randomizes files into indefinite layers. In other words…. It cannot be cracked.
Our process of scrambling data in a non linear fashion creates a practically infinite amount of possible combinations. In fact, those combinations are so vast, that even with a brute force attack, the efforts required to crack the data would take years…if not centuries.
TOTAL CONTROL OF YOUR DATA
Even if your data is stolen, it can only be opened by the owner or intended recipient. XSETTE technology strictly assigns data to particluar devices. This locks out any outside source. Even intercepted data cannot be opened or viewed. This way of approaching content protection is unique and provides a highly secure data environment.
